OpenSSL 介绍
OpenSSL是一个开放源代码的软件库包,应用程序可以使用这个包来进行安全通信,避免窃听,同时确认另一端连线者的身份。这个包广泛被应用在互联网的网页服务器上
其主要库是以C语言所写成,实现了基本的加密功能,实现了SSL与TLS协议。OpenSSL可以运行在OpenVMS、 Microsoft Windows以及绝大多数类Unix操作系统上(包括Solaris,Linux,Mac OS X与各种版本的开放源代码BSD操作系统)
OpenSSL计划在1998年开始,其目标是发明一套自由的加密工具,在互联网上使用。OpenSSL以Eric Young以及Tim Hudson两人开发的SSLeay为基础,随着两人前往RSA公司任职,SSLeay在1998年12月停止开发。因此在1998年12月,社群另外分支出OpenSSL,继续开发下去
OpenSSL管理委员会当前由7人组成有13个开发人员[3]具有提交权限(其中许多人也是OpenSSL管理委员会的一部分)。只有两名全职员工(研究员),其余的是志愿者
该项目每年的预算不到100万美元,主要依靠捐款。 TLS 1.3的开发由Akamai赞助
心脏出血漏洞:OpenSSL 1.0.1版本(不含1.0.1g)含有一个严重漏洞,可允许攻击者读取服务器的内存信息。该漏洞于2014年4月被公诸于世,影响三分之二的活跃网站
包括三个组件:
- libcrypto:用于实现加密和解密的库
- libssl:用于实现ssl通信协议的安全库
- openssl:多用途命令行工具
2.2 Base64 编码
Base64是网络上最常见的用于传输 8Bit 字节码的编码方式之一,Base64就是一种基于64个可打印字符来表示二进制数据的方法
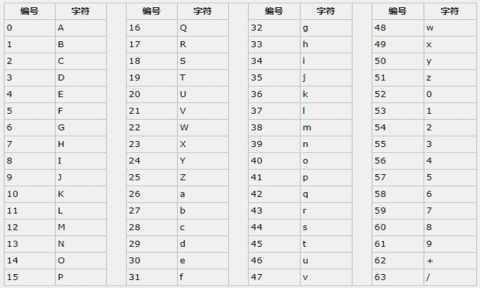
base64的编码过程如下:
将每3个字节放入一个24位的缓冲区中,最后不足3个字节的,缓冲区的剩余部分用0来填补。然后每次取出6位(2的6次方为64,使用64个字符即可表示所有),将高2位用0来填充,组成一个新的字节,计算出这个新字节的十进制值,对应上面的编码表,输出相应的字符。这样不断地进行下去,就可完成对所有数据的编码工作。
按照以上规则对文本Man编码如下:
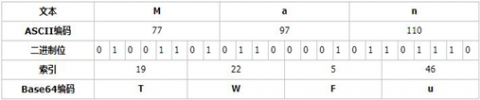
范例:
[root@centos8 ~]#echo -n Man | base64
TWFu
[root@centos8 ~]#echo TWFu | base64 -d
Man[root@centos8 ~]#
[root@centos8 ~]#echo -n ab | base64
YWI=
[root@centos8 ~]#echo -n ab | base64 | base64 -d
ab[root@centos8 ~]#
openssl命令
两种运行模式:
- 交互模式
- 批处理模式
三种子命令:
- 标准命令
- 消息摘要命令
- 加密命令
范例:
[root@centos8 ~]#openssl version
OpenSSL 1.1.1 FIPS 11 Sep 2018
[root@centos8 ~]#openssl help
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
dsa dsaparam ec ecparam
enc engine errstr gendsa
genpkey genrsa help list
nseq ocsp passwd pkcs12
pkcs7 pkcs8 pkey pkeyparam
[root@centos8 ~]#openssl
OpenSSL> help
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
......
OpenSSL> ca --help
Usage: ca [options]
Valid options are:
-help Display this summary
-verbose Verbose output during processing
-config val A config file
......
OpenSSL>q
[root@centos8 ~]#2.3.1 openssl命令对称加密
工具:openssl enc, gpg
算法:3des, aes, blowfish, twofish
enc命令:帮助:man enc
加密:
openssl enc -e -des3 -a -salt -in testfile -out testfile.cipher解密:
openssl enc -d -des3 -a -salt –in testfile.cipher -out testfileopenssl命令单向加密
工具:openssl dgst
算法:md5sum, sha1sum, sha224sum,sha256sum…
dgst命令:帮助:man dgst
openssl dgst -md5 [-hex默认] /PATH/SOMEFILE
openssl dgst -md5 testfile
md5sum /PATH/TO/SOMEFILE补充知识:
MAC: Message Authentication Code,单向加密的一种延伸应用,用于实现网络通信中保证所传输数据的完整性机制
HMAC:hash-based MAC,使用md5或sha1算法
2.3.3 openssl命令生成用户密码
passwd命令:帮助:man sslpasswd
openssl passwd -1 -salt SALT(最多8位)
openssl passwd -1 –salt centos2.3.4 openssl命令生成随机数
随机数生成器:伪随机数字,利用键盘和鼠标,块设备中断生成随机数
/dev/random:仅从熵池返回随机数;随机数用尽,阻塞
/dev/urandom:从熵池返回随机数;随机数用尽,会利用软件生成伪随机数,非阻塞
帮助:man sslrand
openssl rand -base64|-hex NUM
NUM: 表示字节数,使用-hex,每个字符为十六进制,相当于4位二进制,出现的字符数为NUM*2范例:生成随机10位长度密码
[root@centos8 ~]#openssl rand -base64 9 |head -c10
ip97t6qQes[root@centos8 ~]#
[root@centos8 ~]#tr -dc '[:alnum:]' < /dev/urandom |head -c10
DO2mDp3eZu[root@centos8 ~]#openssl命令实现PKI
公钥加密:
算法:RSA, ELGamal
工具:gpg, openssl rsautl(man rsautl)
数字签名:
算法:RSA, DSA, ELGamal
密钥交换:
算法:dh
DSA:Digital Signature Algorithm
DSS:Digital Signature Standard
RSA:
openssl命令生成密钥对儿:man genrsa
生成私钥
openssl genrsa -out /PATH/TO/PRIVATEKEY.FILE NUM_BITS范例:
#生成对称秘钥加密的私钥
(umask 077; openssl genrsa –out test.key –des 2048)
#将加密对称秘钥key解密
openssl rsa -in test.key –out test2.key 从私钥中提取出公钥
openssl rsa -in PRIVATEKEYFILE –pubout –out PUBLICKEYFILE范例:
openssl rsa –in test.key –pubout –out test.key.pub范例:
[root@centos7 ~]#(umask 066;openssl genrsa -out /data/app.key)
Generating RSA private key, 2048 bit long modulus
........................+++
.+++
e is 65537 (0x10001)
[root@centos7 ~]#ls -l /data/
total 4
-rw------- 1 root root 1679 Feb 3 15:26 app.key
[root@centos8 ~]#openssl genrsa -out /data/app.key 1024
Generating RSA private key, 1024 bit long modulus (2 primes)
.............................................................................+++++
..........+++++
e is 65537 (0x010001)
[root@centos8 ~]#ll /data/app.key
-rw------- 1 root root 891 Feb 3 14:52 /data/app.key范例:
[root@centos8 ~]#openssl rsa -in /data/app.key -pubout -out /data/app.key.pub
writing RSA key
[root@centos8 ~]#ls -l /data/
total 8
-rw------- 1 root root 887 Feb 3 15:28 app.key
-rw-r--r-- 1 root root 272 Feb 3 15:32 app.key.pub
[root@centos8 ~]#cat /data/app.key.pub
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCvkS+Z4NWAMoXEwNUyn58J0oI+
ZjXotZUJLfbVHvGd3Ug6Rk52imHp1J629edUn0Cw7KoPfQLegmWsldG4v931HCdl
ELT2vj+QE7KJhc1tGFomzCnX8Q41tRrVVbHPxQYvNmMRXRqIdqXGxFpR758EngxF
zAGcnLTrDz/I2GocrQIDAQAB
-----END PUBLIC KEY-----范例:生成加密的私钥,并解密
[root@centos8 ~]#openssl genrsa -out /data/app.key -des3 1024
Generating RSA private key, 1024 bit long modulus (2 primes)
......+++++
...........+++++
e is 65537 (0x010001)
Enter pass phrase for /data/app.key:
Verifying - Enter pass phrase for /data/app.key:
[root@centos8 ~]#ls -l /data
total 4
-rw------- 1 root root 963 Feb 3 15:27 app.key
[root@centos8 ~]#cat /data/app.key
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,577C3B861BAD86B6
VM8P7vx1UUcSJyXCB0pDO9xgmdNgsMOcl6NitdUvBA9Jx2oLyxsT6TYbbvZvlF55
aQB0bq43atECDBz2+v1ghacPp78S2wuGuTR1hdWwfFKJNr6d/5yXO4y1ZOt3RLvR
E4K6TCeSwZTIUNeQyuh+vstarQmaLQmdObb3lsMG+WipQj3hb0oGdZcWjuQ0gi1B
RKN1duhsWFQbdXZamBqWQqCbvigmqRwjk7S6GE3YwVhys1T4N0BFX/edNCMnzb79
6/mR+LJ2Wz/ecJXB5250rVby3h88ZNsgARg7jUM9zI6jf7G4t1etRlCJ8A9TvDe8
J/5lkDUSWEh1dnB+xw5uamDY7f3GanuKTEe54DxuBwmbBpphV1QTTefSJ01Q6l9K
wS0zV6WE+vCt99dE9J8+GXGD77twRcbmjDWfaoibvwMu00crB9K5dbxdSX50jlD9
Mj+bVr9tcwQW/WzA+V05Ndb74e8OE97pEFjTX8DeIxcZomDUcpNGpQ0eWvyE+A2x
Srux9nN8z9dUF963V4NjQGUg1owQPAlfO6zBGObXnynOqKDmBj+8FfWrnHnZUVt5
3HTV+uSkLuA+8lGoNoxH4/6ZLfvY0Y5+WSg3st2EvwGT74SNNrsNYD0qGt1LujQx
IiwfCI0uv8rqgtLtsYmJmYI0t7hWUVmb6QgX1Qh0Kvzc0A34IMDjY6dhXTKnxeF3
LGkrFAgl3+6tKXxMuQDLB6Jy9m3SOwW/JoXMVVcYHrSPzTgAl2sgAkgEq8nf4yfm
ZP9WHrDe10yXY+5K2h8UiFhvrnQ+YnH4BcTrKuEa9T7pxToo0cTdqg==
-----END RSA PRIVATE KEY-----
[root@centos8 ~]#openssl rsa -in /data/app.key -out /data/app.key
Enter pass phrase for /data/app.key:
writing RSA key
[root@centos8 ~]#ls -l /data
total 4
-rw------- 1 root root 887 Feb 3 15:28 app.key
[root@centos8 ~]#cat /data/app.key
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQCvkS+Z4NWAMoXEwNUyn58J0oI+ZjXotZUJLfbVHvGd3Ug6Rk52
imHp1J629edUn0Cw7KoPfQLegmWsldG4v931HCdlELT2vj+QE7KJhc1tGFomzCnX
8Q41tRrVVbHPxQYvNmMRXRqIdqXGxFpR758EngxFzAGcnLTrDz/I2GocrQIDAQAB
AoGAQ/uDJCGkanSlya8lnumiKqqB1mm7nDWb1ScgOhw2UPubeT06Krqg+WtkXdJQ
VjsoUJoDq+WrU7/IYRDOWayp5Be3EXCdyldSrWu1+wqJ1Vnpk2oUAEyr+lzcHhW1
FNQ/5rb8kIUjR7DZpwnsYJxDygnaKaNKiUiF2FsMX8JcS8ECQQDoZt3zSsXYeR4t
Y9kPPA19npQXx9K4Wv2wsCR904pznzoaJ9Kj+6E/3AdxtXcTD0GiZe8vW+H6WCmW
gB1NpGiRAkEAwWTwO9ZncQnA+X2PYTkizBp/JdEdRjcL/D2g+g3rpL2nLChI56C5
zA4NsJFmblE2uY1OLIJBGExiZP/XS74gXQJBAISTOgYyH48P+OEX1plUPrXsorq2
KUU10wbaVNbauF6g9Lo7AXS+dQxC7pQ1Wsoqp9yGnd28Yrs3U/Ig/5ZtNaECQG+/
kKUy3bDOjwhbCjeGmVnQ0bmbXMwO0MkfH15+HrShtfBpEr9s+w8y66wkSEjkere7
M/m6Bj0xHgX4Y4JryS0CQQChBua8JXCCUGLle7+IEEcgQZSF4PdLrmnhrRG7Qrrg
yd6pPuvd2jAGv5fMhjROmf9MWc4DFiRK0B6dz7OyF9j/
-----END RSA PRIVATE KEY-----建立私有CA实现证书申请颁发
建立私有CA:
- OpenCA:OpenCA开源组织使用Perl对OpenSSL进行二次开发而成的一套完善的PKI免费软件
- openssl
证书申请及签署步骤:
1、生成申请请求
2、RA核验
3、CA签署
4、获取证书
openssl的配置文件:
/etc/pki/tls/openssl.cnf三种策略:match匹配、optional可选、supplied提供
match:要求申请填写的信息跟CA设置信息必须一致
optional:可有可无,跟CA设置信息可不一致
supplied:必须填写这项申请信息
范例:
[root@centos8 ~]#cat /etc/pki/tls/openssl.cnf
#
......
####################################################################
[ ca ]
default_ca = CA_default # The default ca section
####################################################################
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several certs with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
RANDFILE = $dir/private/.rand # private random number file
x509_extensions = usr_cert # The extensions to add to the cert
# Comment out the following two lines for the "traditional"
# (and highly broken) format.
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
default_days = 365 # how long to certify for
default_crl_days= 30 # how long before next CRL
default_md = sha256 # use SHA-256 by default
preserve = no # keep passed DN ordering
policy = policy_match
# For the CA policy
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
# For the 'anything' policy
# At this point in time, you must list all acceptable 'object'
# types.
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
......
创建私有CA
1、创建CA所需要的文件
#生成证书索引数据库文件
touch /etc/pki/CA/index.txt
#指定第一个颁发证书的序列号
echo 01 > /etc/pki/CA/serial 2、 生成CA私钥
cd /etc/pki/CA/
(umask 066; openssl genrsa -out private/cakey.pem 2048)3、生成CA自签名证书
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem选项说明:
-new:生成新证书签署请求
-x509:专用于CA生成自签证书
-key:生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路径范例:生成自签名证书
[root@centos8 ~]#openssl req -utf8 -newkey rsa:1024 -subj "/CN=www.magedu.org" -keyout app.key -nodes -x509 -out app.crt
Generating a RSA private key
...........................+++++
...+++++
writing new private key to 'app.key'
-----
[root@centos8 ~]#openssl x509 -in app.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
39:9e:7c:e3:9a:0f:e3:d3:62:ea:8f:02:c9:cd:1e:f3:4a:77:cb:ff
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = www.magedu.org
Validity
Not Before: Feb 4 15:51:39 2020 GMT
Not After : Mar 5 15:51:39 2020 GMT
Subject: CN = www.magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (1024 bit)
Modulus:
00:e1:7e:41:d5:50:03:07:73:13:b2:62:a6:cf:c0:
61:b1:25:1c:54:56:3e:8f:b3:aa:0e:97:49:50:de:
de:ed:7f:2f:0f:fd:17:22:72:f5:36:19:29:65:ff:
ad:ce:81:10:f3:23:8c:fb:af:32:7b:da:bc:3a:a5:
62:1c:8d:e3:f8:1b:a8:1d:82:86:e0:bc:d6:e1:28:
e0:37:33:16:6c:55:89:76:13:0e:50:37:65:39:da:
90:99:a0:d3:6f:af:4e:8d:34:6c:21:e1:ba:10:86:
8e:fd:fb:e2:83:fe:e7:8c:18:14:dc:f2:7d:6c:37:
fe:4e:e0:8d:99:65:d4:f6:9f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
1F:67:31:48:D6:DA:6E:36:C9:6B:EC:3C:61:85:6A:52:C2:B2:06:17
X509v3 Authority Key Identifier:
keyid:1F:67:31:48:D6:DA:6E:36:C9:6B:EC:3C:61:85:6A:52:C2:B2:06:17
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
4f:75:d5:f8:99:ea:dc:4f:fd:57:05:ba:1e:ad:72:23:ae:b8:
ea:93:1d:43:21:f8:66:cb:85:49:6c:b8:8f:1e:f4:a0:e5:ac:
e5:2e:45:03:33:2f:6a:4a:28:97:30:f0:18:dd:c1:f7:46:0b:
3c:b0:b6:d6:bf:23:7d:3b:74:52:75:61:96:f9:b0:04:99:6c:
52:f4:5d:1c:76:33:52:48:4f:d4:1f:4e:5e:00:0c:18:75:c3:
ef:75:bc:c7:ea:37:6e:34:36:b2:a0:f6:6f:06:69:0a:c6:74:
d8:67:4c:16:81:2a:0b:ea:1c:16:ea:8e:48:dd:ba:0b:67:69:
19:1e
[root@centos8 ~]#申请证书并颁发证书
1、为需要使用证书的主机生成生成私钥
(umask 066; openssl genrsa –out /data/test.key 2048)2、为需要使用证书的主机生成证书申请文件
openssl req -new -key /data/test.key -out /data/test.csr3、在CA签署证书并将证书颁发给请求者
openssl ca -in /tmp/test.csr –out /etc/pki/CA/certs/test.crt -days 100注意:默认要求 国家,省,公司名称三项必须和CA一致
4、查看证书中的信息:
openssl x509 -in /PATH/FROM/CERT_FILE -noout -text|issuer|subject|serial|dates
#查看指定编号的证书状态
openssl ca -status SERIAL 吊销证书
在客户端获取要吊销的证书的serial
openssl x509 -in /PATH/FROM/CERT_FILE -noout -serial -subject在CA上,根据客户提交的serial与subject信息,对比检验是否与index.txt文件中的信息一致,吊销证书:
openssl ca -revoke /etc/pki/CA/newcerts/SERIAL.pem指定第一个吊销证书的编号,注意:第一次更新证书吊销列表前,才需要执行
echo 01 > /etc/pki/CA/crlnumber更新证书吊销列表
openssl ca -gencrl -out /etc/pki/CA/crl.pem查看crl文件:
openssl crl -in /etc/pki/CA/crl.pem -noout -textCentOS 7 创建自签名证书
[root@centos7 ~]#cd /etc/pki/tls/certs
[root@centos7 certs]#make
This makefile allows you to create:
o public/private key pairs
o SSL certificate signing requests (CSRs)
o self-signed SSL test certificates
To create a key pair, run "make SOMETHING.key".
To create a CSR, run "make SOMETHING.csr".
To create a test certificate, run "make SOMETHING.crt".
To create a key and a test certificate in one file, run "make SOMETHING.pem".
To create a key for use with Apache, run "make genkey".
To create a CSR for use with Apache, run "make certreq".
To create a test certificate for use with Apache, run "make testcert".
To create a test certificate with serial number other than random, add SERIAL=num
You can also specify key length with KEYLEN=n and expiration in days with DAYS=n
Any additional options can be passed to openssl req via EXTRA_FLAGS
Examples:
make server.key
make server.csr
make server.crt
make stunnel.pem
make genkey
make certreq
make testcert
make server.crt SERIAL=1
make stunnel.pem EXTRA_FLAGS=-sha384
make testcert DAYS=600
[root@centos7 certs]#ls
ca-bundle.crt ca-bundle.trust.crt make-dummy-cert Makefile renew-dummy-cert
[root@centos7 certs]#cat Makefile
UTF8 := $(shell locale -c LC_CTYPE -k | grep -q charmap.*UTF-8 && echo -utf8)
DAYS=365
KEYLEN=2048
TYPE=rsa:$(KEYLEN)
EXTRA_FLAGS=
ifdef SERIAL
EXTRA_FLAGS+=-set_serial $(SERIAL)
endif
.PHONY: usage
.SUFFIXES: .key .csr .crt .pem
.PRECIOUS: %.key %.csr %.crt %.pem
usage:
@echo "This makefile allows you to create:"
@echo " o public/private key pairs"
@echo " o SSL certificate signing requests (CSRs)"
@echo " o self-signed SSL test certificates"
@echo
@echo "To create a key pair, run \"make SOMETHING.key\"."
@echo "To create a CSR, run \"make SOMETHING.csr\"."
@echo "To create a test certificate, run \"make SOMETHING.crt\"."
@echo "To create a key and a test certificate in one file, run \"make SOMETHING.pem\"."
@echo
@echo "To create a key for use with Apache, run \"make genkey\"."
@echo "To create a CSR for use with Apache, run \"make certreq\"."
@echo "To create a test certificate for use with Apache, run \"make testcert\"."
@echo
@echo "To create a test certificate with serial number other than random, add SERIAL=num"
@echo "You can also specify key length with KEYLEN=n and expiration in days with DAYS=n"
@echo "Any additional options can be passed to openssl req via EXTRA_FLAGS"
@echo
@echo Examples:
@echo " make server.key"
@echo " make server.csr"
@echo " make server.crt"
@echo " make stunnel.pem"
@echo " make genkey"
@echo " make certreq"
@echo " make testcert"
@echo " make server.crt SERIAL=1"
@echo " make stunnel.pem EXTRA_FLAGS=-sha384"
@echo " make testcert DAYS=600"
%.pem:
umask 77 ; \
PEM1=/bin/mktemp /tmp/openssl.XXXXXX ; \ PEM2=/bin/mktemp /tmp/openssl.XXXXXX ; \ /usr/bin/openssl req $(UTF8) -newkey $(TYPE) -keyout $$PEM1 -nodes -x509 -days $(DAYS) -out $$PEM2 $(EXTRA_FLAGS) ; \ cat $$PEM1 > $@ ; \ echo "" >> $@ ; \ cat $$PEM2 >> $@ ; \ $(RM) $$PEM1 $$PEM2 %.key: umask 77 ; \ /usr/bin/openssl genrsa -aes128 $(KEYLEN) > $@ %.csr: %.key umask 77 ; \ /usr/bin/openssl req $(UTF8) -new -key $^ -out $@ %.crt: %.key umask 77 ; \ /usr/bin/openssl req $(UTF8) -new -key $^ -x509 -days $(DAYS) -out $@ $(EXTRA_FLAGS) TLSROOT=/etc/pki/tls KEY=$(TLSROOT)/private/localhost.key CSR=$(TLSROOT)/certs/localhost.csr CRT=$(TLSROOT)/certs/localhost.crt genkey: $(KEY) certreq: $(CSR) testcert: $(CRT) $(CSR): $(KEY) umask 77 ; \ /usr/bin/openssl req $(UTF8) -new -key $(KEY) -out $(CSR) $(CRT): $(KEY) umask 77 ; \ /usr/bin/openssl req $(UTF8) -new -key $(KEY) -x509 -days $(DAYS) -out $(CRT) $(EXTRA_FLAGS) [root@centos7 certs]# [root@centos7 certs]#make app.crt umask 77 ; \ /usr/bin/openssl genrsa -aes128 2048 > app.key Generating RSA private key, 2048 bit long modulus ...............+++ ............................................+++ e is 65537 (0x10001) Enter pass phrase: Verifying - Enter pass phrase: umask 77 ; \ /usr/bin/openssl req -utf8 -new -key app.key -x509 -days 365 -out app.crt Enter pass phrase for app.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:hubei Locality Name (eg, city) [Default City]:wuhan Organization Name (eg, company) [Default Company Ltd]:magedu Organizational Unit Name (eg, section) []:it Common Name (eg, your name or your server's hostname) []:www.magedu.org Email Address []:admin@magedu.org [root@centos7 certs]#ls app.crt app.key ca-bundle.crt ca-bundle.trust.crt make-dummy-cert Makefile renew-dummy-cert [root@centos7 certs]#openssl x509 -in app.crt -noout -text Certificate: Data: Version: 3 (0x2) Serial Number: 90:d7:97:6a:21:21:f8:5e Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=hubei, L=wuhan, O=magedu, OU=it, CN=www.magedu.org/emailAddress=admin@magedu.org Validity Not Before: Feb 5 00:28:31 2020 GMT Not After : Feb 4 00:28:31 2021 GMT Subject: C=CN, ST=hubei, L=wuhan, O=magedu, OU=it, CN=www.magedu.org/emailAddress=admin@magedu.org Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:f8:dd:d3:ea:0b:f1:97:0f:27:de:44:a2:32:77: fb:5c:73:74:17:7b:5f:a4:9c:a2:d4:3b:d4:49:4c: da:e0:a2:6a:41:05:6e:10:1e:96:dc:95:34:ed:08: 05:18:ba:27:c5:e5:f0:7c:65:15:78:f8:9b:bf:ee: 41:ef:1c:6f:7f:35:29:fd:f5:cf:4a:f1:36:7e:0c: 37:96:b1:01:e5:aa:7f:6e:a0:56:b0:33:28:ed:db: 7a:56:34:67:83:be:bd:ad:3d:e7:80:d9:cf:6a:c7: c9:7f:d1:83:73:33:7f:77:27:a5:2e:17:84:82:c7: 50:3d:20:d8:20:f1:5e:61:d2:69:07:8f:0e:cd:ea: c2:51:bd:aa:a0:ce:61:18:6f:00:43:13:21:8d:6d: 3b:85:13:d8:93:ed:fc:65:28:ec:12:d1:67:40:d0: 98:54:9a:59:1e:10:4f:c5:8c:b5:b1:26:55:2f:e1: 53:1d:6b:71:88:64:e2:b1:21:28:8c:c7:04:3a:70: 87:c7:48:41:44:95:43:2f:e8:da:5f:f8:93:1a:9a: de:e4:e3:82:57:60:6a:49:08:2e:5f:57:f7:62:b2: bb:8a:1f:8b:2b:dc:40:dd:35:30:42:c1:f4:c6:1a: 0b:61:df:37:ed:bd:25:39:4c:5f:27:32:57:9e:d0: 11:9d Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: 28:48:D7:B5:02:7E:D7:4B:A1:74:A7:86:4B:3C:E5:FC:39:7B:F4:2E X509v3 Authority Key Identifier: keyid:28:48:D7:B5:02:7E:D7:4B:A1:74:A7:86:4B:3C:E5:FC:39:7B:F4:2E X509v3 Basic Constraints: CA:TRUE Signature Algorithm: sha256WithRSAEncryption a3:66:1b:85:dc:9e:1b:c7:c8:e4:29:3c:32:b2:fc:71:c9:79: 9e:ad:db:78:bd:a4:42:1a:ef:d7:7f:4a:84:d9:46:e1:60:fa: 9f:04:83:67:88:74:fd:99:d2:e3:7b:34:86:27:a1:d0:3c:be: 5f:93:d0:17:e9:d1:f6:19:2b:d5:e7:48:1f:56:ac:65:22:ec: 64:6f:a3:05:0c:83:2f:29:a8:ef:cc:25:51:d0:16:21:93:9e: 85:fc:82:d4:8c:ba:14:47:6e:fd:33:44:71:a7:c4:7f:92:2a: 01:40:f9:69:70:73:27:89:73:82:ea:21:95:48:e2:c1:5d:b8: ed:e7:61:49:88:1c:b6:8a:a6:bd:cc:83:6b:2c:19:b9:07:21: 46:f8:1f:dc:cb:3c:9c:6d:b9:b1:dc:03:b0:5a:00:de:41:7c: 96:d8:3a:f3:06:fc:24:03:60:54:35:85:a2:1e:79:fc:cb:6e: fd:e2:c3:7b:16:6e:7c:56:17:d4:64:c9:15:e9:a4:b0:9a:a7: c5:d6:f8:c8:e4:99:b1:b0:f0:8b:b4:ea:8e:a9:29:c1:4a:19: 69:7a:d7:51:93:23:51:b6:0b:63:e1:45:a7:3f:65:4d:89:55: e8:52:29:0a:41:d2:fb:76:20:7e:14:da:a8:ad:e6:fc:b0:a9: 5f:10:b0:d3 [root@centos7 certs]#


